Introduction:
What is Conditional Access?
Conditional Access is a feature of Azure AD that helps organizations improve security and compliance. By creating Conditional Access policies, you can fine-tune your authentication process — without unduly burdening users.
Azure AD Conditional Access helps you strengthen your authentication process in a way that avoids issues like these.
For example, you can create a policy to require administrators — but not regular business users — to complete an MFA step. But you can get a lot more granular than that. You’re not limited to simple facts like whether the user is an admin; you can also factor in things like the user’s location and the type of authentication protocol being used. For instance, you can deny all requests that come from North Korea, allow all requests that come from your headquarters location, and require MFA for all the rest. Moreover, you can create multiple policies that work together to put guardrails in place exactly where you need them.
Components of an Azure AD Conditional Access policy
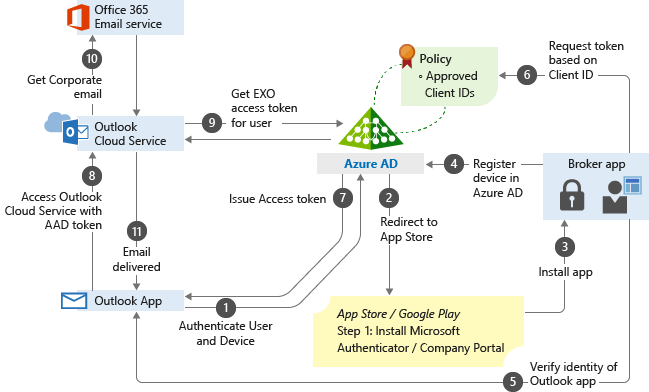
Assignments:
- Users and groups :The Users and groups section specifies who the policy will include or exclude. A policy might apply all users, all Finance team members, or just B2B guests and external users.
- Cloud apps or actions : You can also specify which cloud apps or actions the policy will include or exclude. For example, you can create a policy that applies anyone accessing Office 365 and one that applies only to folks trying to use PowerApps.
- Conditions: A policy must contain one or more conditions, which are sometimes also called signals. These include the device’s operating system, location and client apps, as well as risk information from Microsoft Identity Protection (if you have an Azure AD Premium P2 license). Multiple conditions can be combined to create very fine-grained policies.
Access controls:
Enable policy:
Does organization need Azure AD Conditional Access?
Now that we’ve covered what Conditional Access does, let’s tackle the harder question:
Who needs it and who doesn’t?
There’s no doubt that Azure AD Conditional Access policies can be valuable, but they do require setup, thorough testing and ongoing maintenance. Before you make that investment of time and effort, be sure to review the security that Microsoft provides out of the box.
To help organizations establish a basic level of security, Microsoft makes security defaults available to everyone at no extra cost. New tenants get security defaults automatically. For older tenants, you can turn on security defaults in the Azure portal. This feature automatically enforces the following policies:
• All users must register for Azure AD MFA.
•Users must complete an MFA step when they authenticate using a new device or application, and when the request to perform critical tasks.
•Administrators must complete an MFA step every time they sign in. This policy applies to nine key Azure AD roles, including Global Administrator, SharePoint Administrator, Exchange Administrator, Conditional Access Administrator and Security Administrator.
• Any user trying to access the Azure portal, Azure PowerShell or the Azure CLI must complete additional authentication.
• All authentication requests made using older protocols are blocked.
How do I set up Conditional Access?
How to create a Conditional Access policy
1.Navigate to Azure Active Directory > Security > Conditional Access.
2. Click New policy.
3. Give your policy a name and complete the other three critical elements of Conditional Access (Assignments, Access controls and Enable policy) as described earlier in this blog post.
4. Click.