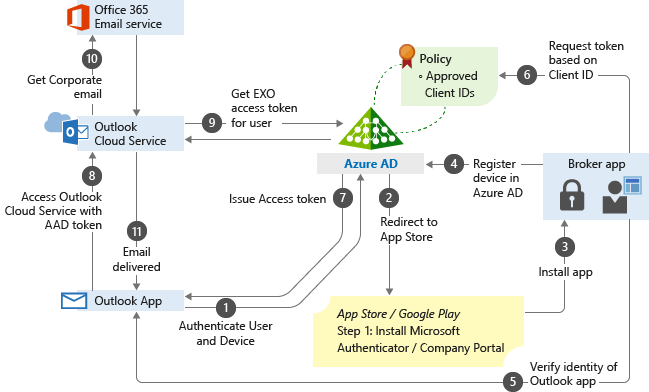
Introduction:
In today’s digital era, businesses and individuals alike rely heavily on the power of cloud computing to run their applications and services efficiently. Microsoft Azure, one of the leading cloud platforms, offers a wide range of services to cater to diverse computing needs. Among these services, Azure Virtual Machines (VMs) stand out as a versatile and powerful tool that enables users to deploy and manage their applications in a flexible and scalable environment. In this blog post, we will explore the benefits and features of Azure Virtual Machines and how they can empower your applications.
Azure Virtual Machines are essentially virtualized instances of computers running various operating systems (such as Windows or Linux) within the Azure cloud. These VMs offer an environment that closely resembles a physical computer, allowing you to install and run software, host websites, store data, and perform other computing tasks.
Why businesses find Azure Virtual Machines beneficial?
• Scalability: One of the key advantages of Azure VMs is their ability to scale resources up or down based on demand. Whether you need to increase processing power, memory, or storage, Azure VMs provide the flexibility to adjust resources to match your application’s requirements.
• Cost Efficiency: Azure VMs offer a pay-as-you-go pricing model, allowing you to pay only for the resources you consume. This cost-effective approach eliminates the need for upfront hardware investments and enables you to optimize your budget.
• Wide Range of Operating Systems: Azure VMs support a broad spectrum of operating systems, including Windows, Linux, and various distributions. This flexibility allows you to choose the OS that best suits your application and development stack.
• Integration with Azure Services: Azure Virtual Machines seamlessly integrate with other Azure services, such as Azure Storage, Azure Networking, and Azure Active Directory. This integration simplifies the deployment and management of your applications, providing a comprehensive ecosystem to support your needs.
Use Cases for Azure Virtual Machines:
• Development and Testing: Azure VMs are ideal for creating development and testing environments. You can quickly spin up VMs with specific configurations, test your applications, and easily replicate the production environment.
• Web Hosting: Whether you’re running a personal blog or hosting enterprise websites, Azure VMs provide a reliable and scalable platform. You can choose from various VM sizes and configurations to handle different levels of traffic and performance requirements.
• Data Analytics: Azure VMs are well-suited for running data analytics workloads. You can leverage the power of Azure’s data services, such as Azure Data Lake Storage and Azure Databricks, to process large datasets and gain valuable insights.
• Hybrid Scenarios: Azure VMs seamlessly integrate with on-premises infrastructure, enabling hybrid cloud scenarios. You can extend your existing data centre to Azure, ensuring a smooth transition and enabling hybrid application architectures.
Getting Started with Azure Virtual Machines:
To get started with Azure VMs, you can follow these steps:
1. Create an Azure account and set up your subscription.
2. Access the Azure portal or use Azure CLI/PowerShell to provision a new virtual machine.
3. Choose the desired VM size, operating system, and additional configurations.
4. Configure networking, storage, and security settings for your VM.
5. Install and deploy your applications on the VM and start leveraging the power of Azure.
Conclusion:
Azure Virtual Machines offer a powerful and flexible computing environment within the Azure cloud. By harnessing the scalability, cost efficiency, and extensive integration capabilities of Azure VMs, you can empower your applications to reach new heights. Whether you’re a developer, a small business owner, or an enterprise, Azure VMs provide the tools and resources to optimize your workloads, enhance performance.